ATM Physical Attacks on the Rise
There continues to be an increase in physical security attacks of ATMs in multiple locations across the United States. In these types of attacks, a large vehicle with a hook-and-chain assembly attached is used to rip the safe door from the terminal. Attackers place a hook or hooks connected to the chain into the safe door openings of front-loading terminals where the horizontal transport or depository module extends through the safe’s door. They then use the vehicle attached to the chain to pull the safe’s door from the unit. Terminals with this configuration placed in a way that makes them more easily accessible by a vehicle are more likely to be targeted.
Criminals have successfully attacked drive-up, front-loading terminals configured with horizontal cash transports or depository modules that extend through the safe door. Typically, the attacks occur in 5 minutes or less.
To enhance security regarding this threat, consider the following:
Deter the Attack
Complete physical security crime risk assessments pre-installation to determine crime risk, verify appropriate machine type and the best location for placement. Conduct regular physical security crime risk assessments to evaluate, respond to and mitigate changes in risk throughout the life cycle of the ATM.
Install new ATMs in areas of high visibility.
Ensure lighting at and surrounding new and existing ATMs is compliant with local/state regulations and internal lighting standards.
Specifically, regarding hook and chain attacks, consider replacing terminals in high-risk areas with a new depository and cash-over-keyboard model to prevent the possibility of attaching a hook to the safe’s door.
Delay the Attack
Implement safe door reinforcement (aka blocker) kits for terminals at risk. These hook and chain protective kits add reinforcement to the safe door’s cash dispenser and depository slots and minimize gaps to block hook or chain access points.
Financial institutions and independent deployers should install ATMs in areas with an orientation that prevents runway access for vehicles. Reducing runway access prevents the vehicle from creating enough speed to weaken or remove the safe door. In addition, consider using bollards, obstacles, or other physical barriers to minimize open areas in proximity of the ATM that would give a vehicle the space needed to enter, rapidly pull away from, and repeatedly attempt hook and chain attacks. Protection especially applies to any open space perpendicular to the front of the ATM.
Consider higher grade safes that additionally delay attackers and decrease the likelihood of a successful attack.
Implement bollard barriers that cover the safe door to minimize the effectiveness of this attack.
Detect the Attack
Implement measures to detect these attacks based on sensors, alarm systems, video surveillance and their connection to a 24/7 security monitoring center or SOC.
Respond to the Attack
If an attacker does gain access to the cash cassettes inside the safe, the use of ink staining solutions will deface the cash.
Install GPS trackers to alert authorities and aid in the recovery of stolen funds if the attack is successful.
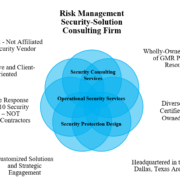
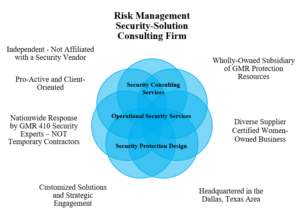
Engage with GMR 410’s Security Experts
Our Security Experts have decades of experience in ATM security. Contact us to schedule a free initial consultation to help identify solutions for protecting your ATMs.









 vulnerabilities and mitigation techniques, to be ever evolving and scattered across a multitude of sources and sites. With this white paper, I aimed to summarize and consolidate information in plain language so security professionals and independent ATM operators can spend less time searching the internet and other resources and more time planning their asset protection strategy.”
vulnerabilities and mitigation techniques, to be ever evolving and scattered across a multitude of sources and sites. With this white paper, I aimed to summarize and consolidate information in plain language so security professionals and independent ATM operators can spend less time searching the internet and other resources and more time planning their asset protection strategy.”


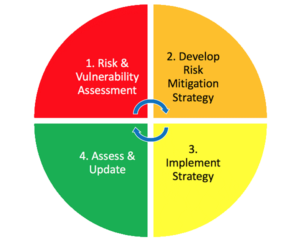
 Banks and other financial institutions are faced with the critical challenge of ensuring the protection of their people, assets and information. Security officers should utilize an ongoing assessment program to monitor and respond to changing risks and threats.
Banks and other financial institutions are faced with the critical challenge of ensuring the protection of their people, assets and information. Security officers should utilize an ongoing assessment program to monitor and respond to changing risks and threats.
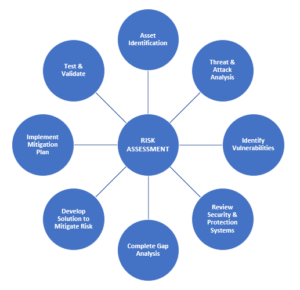 From insider threats to external forces, it is important for security professionals to remain vigilant in their understanding of the risks, threats and vulnerabilities in and to their organizations.
From insider threats to external forces, it is important for security professionals to remain vigilant in their understanding of the risks, threats and vulnerabilities in and to their organizations. You may be thinking, “I thought threats and risk are the same. What do you mean when you talk about vulnerabilities?” Threats, risks, and vulnerability are not interchangeable terms. Rather, they are the essential ingredients of an accurate risk analysis. In their simplicity,
You may be thinking, “I thought threats and risk are the same. What do you mean when you talk about vulnerabilities?” Threats, risks, and vulnerability are not interchangeable terms. Rather, they are the essential ingredients of an accurate risk analysis. In their simplicity,

 Hurricane or Tropical Storm Watch: Hurricane or tropical storm conditions are possible in the specified area of the watch, usually within 48 hours. Individuals inside the Watch area should monitor updates from NOAA and local radio/television.
Hurricane or Tropical Storm Watch: Hurricane or tropical storm conditions are possible in the specified area of the watch, usually within 48 hours. Individuals inside the Watch area should monitor updates from NOAA and local radio/television.




